Developer Zero Trust is not a new security framework and not a replacement for IAM, CI/CD controls, or traditional Zero Trust architectures.
It is the application of Zero Trust principles to software development by ensuring that no developer action is implicitly trusted, and that risk is always attributable to identity and behavior—human or AI.
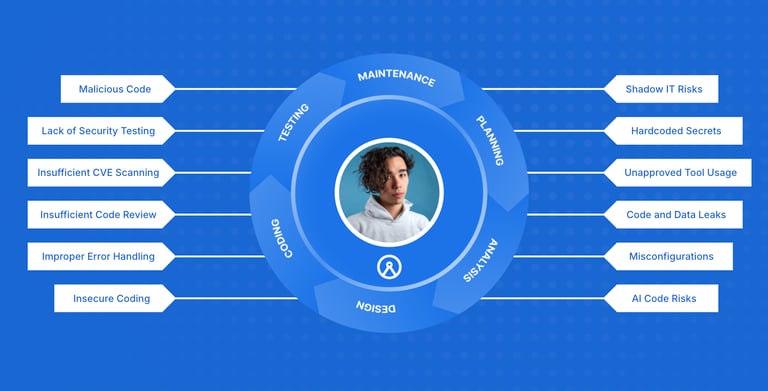
In practice, Developer Zero Trust is enabled through Developer Security Posture Management (DevSPM), which acts as the system of record linking scan results, vulnerabilities, and policy violations to developer identity and actions across the SDLC.
This allows organizations to:
Continuously validate developer and AI activity across the SDLC
Attribute vulnerabilities and security findings to identity and action
Govern tool usage without disrupting developer velocity
Preserve audit-ready evidence tied to developer behavior
Without developer-aware visibility, Zero Trust programs cannot extend meaningfully into development workflows.
Traditional Zero Trust implementations focus on network access, endpoints, and runtime systems. However, when risk is introduced during development, security teams often cannot answer:
Who introduced this vulnerability?
Was it human-written code, AI-assisted, or autonomous?
Which tool or workflow introduced the risk?
Is this behavior recurring across teams?
This gap leaves organizations exposed to:
Insider Threats. Compromised credentials or misuse of access can introduce risk long before deployment—often without detection.
Shadow IT. Unapproved developer tools, IDE plugins, or CI/CD integrations expand the attack surface without visibility.
Risky Development Behaviors. Insecure dependencies, mishandled secrets, or flawed AI-generated code can silently propagate risk across repositories.
Developer Zero Trust requires identity-aware telemetry to validate every action, not just runtime access.
Security incidents repeatedly demonstrate how development-stage risk bypasses traditional Zero Trust controls:
Credential Mismanagement and Insider Risks: The Uber breach (2022) demonstrated how compromised developer credentials could provide attackers with access to critical internal systems, exposing user data.
AI-Generated Code Vulnerabilities: In 2024, research revealed that AI tools like GitHub Copilot sometimes suggested insecure code solutions. With Zero Trust SDLC, AI-assisted development undergoes rigorous validation to ensure safe implementation.
These events reinforce the need for Zero Trust principles before code reaches production.
Archipelo enables Developer Zero Trust by making developer actions observable across the SDLC—human and AI—through Developer Security Posture Management.
Archipelo creates a historical record of coding events tied to developer identity and actions, providing the attribution and context required for continuous validation.
Key Capabilities:
Developer Vulnerability Attribution
Trace scan results and vulnerabilities to the developers and AI agents who introduced them.Automated Developer & CI/CD Tool Governance
Scan developer and CI/CD tools to verify tool inventory and mitigate shadow IT risks.AI Code Usage & Risk Monitor
Monitor AI code tool usage to ensure secure and responsible software development.Developer Security Posture
Generate insights into security risks introduced by developer actions across individuals and teams.
These capabilities provide the foundation required to apply Zero Trust principles within the SDLC—without redefining existing Zero Trust architectures.
Developer Zero Trust is not enforced through blanket restrictions or developer surveillance.
It is achieved by making developer actions attributable, auditable, and governable.
By enabling Developer Security Posture Management, organizations can:
Validate every developer action
Reduce investigation time through identity-based attribution
Strengthen compliance evidence
Prevent recurring risk by addressing root cause
Archipelo strengthens existing ASPM and CNAPP stacks with developer-level observability and telemetry—enabling Zero Trust outcomes where software risk actually originates.
Contact us to learn how Archipelo strengthens your existing ASPM and CNAPP stack with Developer Security Posture Management.